In the recent years, we have heard of many people and big corporates losing their precious data or being in a situation where their systems are hacked. These unwanted activities are being caused, in most of the cases, using a piece of software inserted into a network system, server or a personal computer. This piece of software is known as a malware.
A malware can cause harm to a system or a network directly, or subvert them to be used by others, rather than as intended by their owners. It is a combination of two words: Mal meaning Bad and Ware meaning Software.
Based on www.av-test.org, the statistics are growing tremendously. Please look at the following graph to understand the growth of Malware.
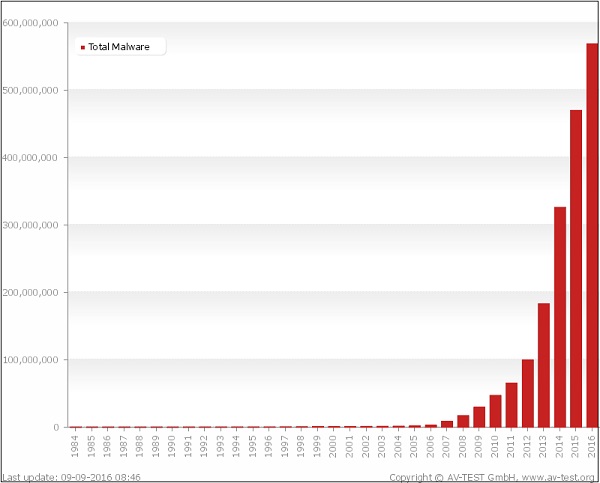
As you can see, there were more than 600,000,000 malwares detected in 2016 alone. Based on securelist.com, the countries that have infected computers compared to the cleaner ones are −
| Maximum risk (over 60%) 22 countries including | ||
|---|---|---|
| Kyrgyzstan (60.77%) | Afghanistan (60.54%). | |
| High risk (41-60%): 98 countries including | ||
| India (59.7%) | Egypt (57.3%) | Belarus (56.7%) |
| Turkey (56.2%) | Brazil (53.9%) | China (53.4%) |
| UAE (52.7%) | Serbia (50.1%) | Bulgaria (47.7%) |
| Argentina (47.4%) | Israel (47.3%) | Latvia(45.9%) |
| Spain (44.6%) | Poland (44.3%) | Germany (44%) |
| Greece (42.8%) | France (42.6%) | Korea (41.7%), |
| Austria (41.7%) | ||
| Moderate local infection rate (21-40.99%): 45 countries including | ||
| Romania(40%) | Italy (39.3%) | Canada (39.2%) |
| Australia (38.5%) | Hungary (38.2%) | Switzerland (37.2%) |
| USA (36.7%) | UK (34.7%) | Ireland (32.7%) |
| Netherlands(32.1%), | Czech Republic (31.5%) | Singapore (31.4%) |
| Norway (30.5%) | Finland (27.4%) | Sweden (27.4%), |
| Denmark (25.8%), | Japan (25.6%). | |
Malware can be designed from the hackers for different purposes like destroying data, sending the data automatically to some other place, altering the data or can keep monitoring it until the specified time-period. Disable security measures, damage the information system, or otherwise affect the data and system integrity.
They also come in different types and forms, which we will discuss in detail in the upcoming chapters of this tutorial.
Malware Removal - How It Works
To understand how malware works, we should first see the anatomy of a malware attack, which is separated in five steps as shown below −
- Entry point
- Distribution
- Exploit
- Infection
- Execution
Let us understand the above-mentioned points in detail.
Entry Point
A malware can enter into the system in many ways −
- The user visits his favorite website that has been infected recently. This can be an entry point for a malware.
- If a user clicks on a URL that has come in an email, it will hijack that browser.
- Malware can also enter through any infected external media such as a USB or an external hard drive.
Distribution
The malware initiates a process that redirects the traffic to an exploit server which checks the OS and applications such as the browser, Java, Flash player, etc.
Exploit
In this phase, the exploit will try to execute based on the OS and will find a way to escalate the privilege.
Infection
Now, the exploit that was successfully installed will upload a payload to maintain access and to manage the victim like remote access, file upload/download, etc.
Execution
In this phase, the hacker who manages the Malware will start to steal your data, encrypt your files, etc.
Malware Removal - Types
Malwares are diverse; they come from different functions and behave differently under various situations. Some of the most infamous and dangerous types of malwares are given below:
- Virus
- Adware
- Spyware
- Trojan
- Rootkits
- Botnets
- Ransom Ware
Let us understand each of these in detail.
Virus
Virus is a malware program that acts in an interesting way. This program executes or replicates itself by putting-in some copies of itself in other computer programs, boot sector, data files, hard disk, etc. When the replication process is done, then the areas that are affected are said to be the infected ones.
Viruses are built to perform some of the most harmful activities on the hosts when they are infected. They can steal the CPU time or even the space in the hard disk. They can also corrupt the data and can put some funny messages on the screen of the system.
Adware
This software is mainly the advertising supporting software. A package that comes automatically with the advertisements inside. Hence, it can generate some good income for the owner.
Spyware
Spyware is a software that is mainly used for the gathering of information about some organization or a person. That information is gathered without anyone getting to know that the information is being fathered from his or her system.
Trojan
Trojan is a non-self-replicating type of malware. It contains some malicious code, which carries out some actions that are determined by the nature of that specific Trojan. This happens upon the execution only. The result of the action is normally the data loss and it can also harm the system in many ways.
Rootkits
Rootkits are the stealth type of malware. They are designed in some special way that they can actually hide themselves very well and it is quite difficult to detect them in a system. The normal methods of detection do not work on them.
Botnets
Botnet is a software installed on a computer that is connected through the internet and it can help one communicate with the other same type of programs, so that some actions can be performed. They can be same as keeping control of some IRC, which are Internet Related Charts. In addition, it can be utilized for sending out some spam emails or to participate in some distribution of denial of services attacks.
Ransom Ware
Ransom ware is a software that encrypts files, which are on the hard drives. Some of them can even end up with simply showing some message about payment of money to the person, who has implemented this program.
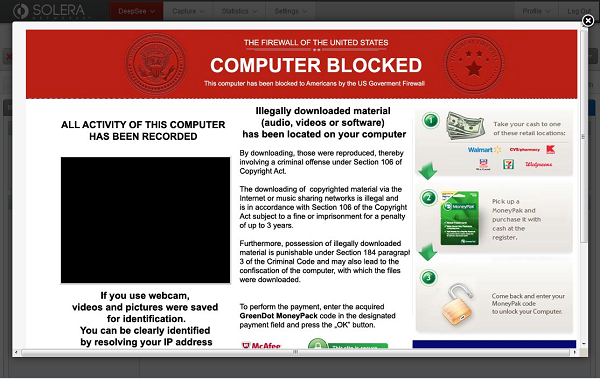
Malware Removal - Detection Techniques
Generally, if a computer is infected there are some symptoms, which even simpler users can notice.
Common Malware Detection Techniques
Some of the most commonly used Malware Detection Techniques are listed as follows.
- Your computer shows a pop-up and error message.
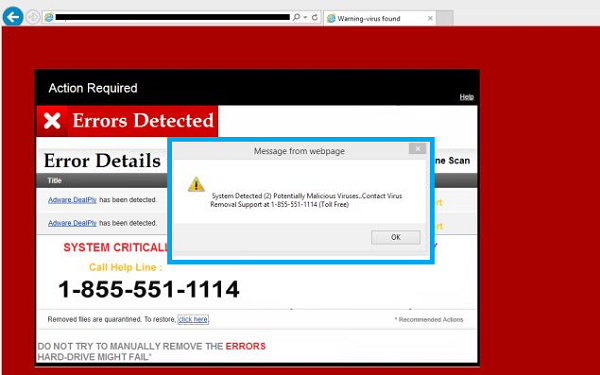
- Your computer freezes frequently and you are unable to work on it.
- The computer slows down when a program or process starts. This can be noticed in the task manager that the process of the software has started, but it has not opened yet for working.
- Third parties complain that they are receiving invitation in social media or via emails from you.
- File extensions changes appear or files are added to your system without your consent.
- Internet explorer freezes too often even though your internet speed is very good.
- Your hard disk is accessed most of the time, which you can see from the blinking LED light of your computer.

- OS files are corrupted or missing.
- If your computer is consuming too much bandwidth or network resources, it is the case of a computer worm.
- Hard disk space is occupied all the time, even if you are not taking any action. For example, a Mew Program installing.
- Files and program sizes change as compared to their original version.
Errors not related to Malware
The following errors are not related to Malware Activities −
- Error while the system is booting in the Bios stage, like Bios’ battery cell display, timer error display.
- Hardware errors like Beeps, RAM burn, HDD, etc.
- If a document fails to start normally like a corrupted file, but the other files can be opened accordingly.
- Keyboard or mouse does not answer your commands; you have to check the plug-ins.
- Monitor switching on and off too often, like blinking or vibrating, this is a hardware fault.
In the next chapter, we will understand how to prepare for Malware removal.
Malware Removal - Preparation for Removal
Malwares attach themselves to programs and transmit to other programs by making use of some events. They need these events to happen because they cannot start by themselves, transmit themselves by using non-executable files and infect other networks or a computer.
To prepare for the removal phase, we should first understand which all computer processes are being used by the malware in order to kill them. Which traffic ports are being used by them in order to block them? What are the files related to these malwares, so we can have the chance to repair them or delete. All this includes a bunch of tools that will help us to gather this information.
Investigation Process
From the above-mentioned conclusions, we should know that when some unusual processes or services run by themselves, we should investigate further their relations with a possible virus. The investigation process is as follows −
To investigate the processes, we should start by using the following tools −
- fport.exe
- pslist.exe
- handle.exe
- netstat.exe
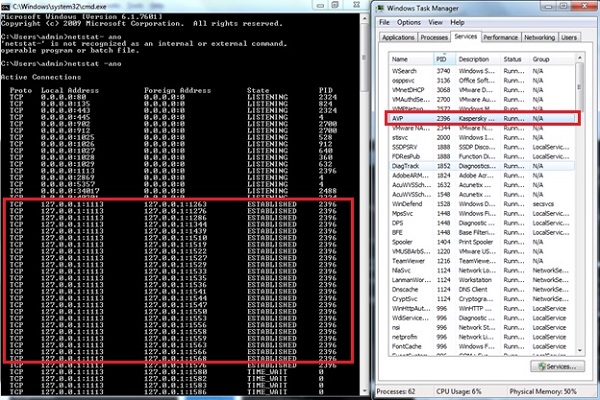
The Listdll.exe shows all the dll files that are being used. The netstat.exewith its variables shows all the processes being run with their respective ports. The following example shows, how a process of Kaspersky Antivirus is mapped to a command netstat-ano to see the process numbers. To check which process number it belongs to, we will use the task manager.
For Listdll.exe, we have download it from the following link – https://technet.microsoft.com/en-us/sysinternals/bb896656.aspx and we can run it to check which processes are connected with the DLL that are being used.
We open CMD and go to the path of Listdll.exe as shown in the following screenshot, then run it.
We will get the result as shown in the following screenshot.
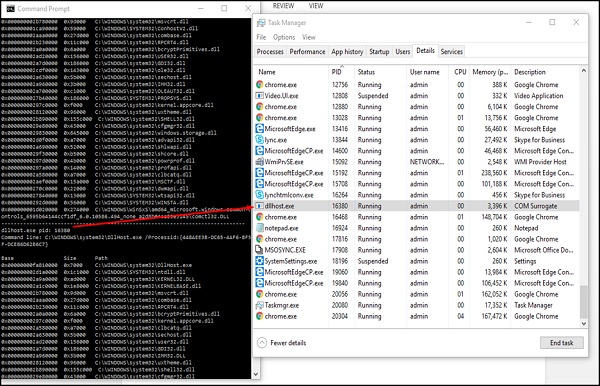
For example, PID 16320 is being used by the dllhost.exe, which has a description COM Surrogate and on the left. It has shown all the DLL being shown by this process, which we can google and check.
Now we will use the Fport, which can be downloaded from the following link – https://www.mcafee.com/hk/downloads/free-tools/fport.aspx# to map the services and PID with the ports.
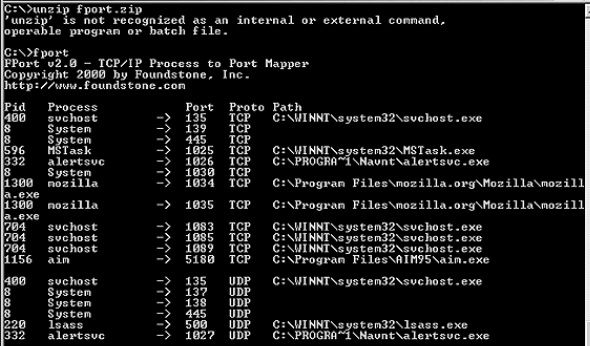
Another tool to monitor the services and to see how many resources they are consuming is called as the “Process Explorer”, which can be downloaded from the following link – https://download.sysinternals.com/files/ProcessExplorer.zip and after downloading it, you have to run the exe file and you will see the following result −
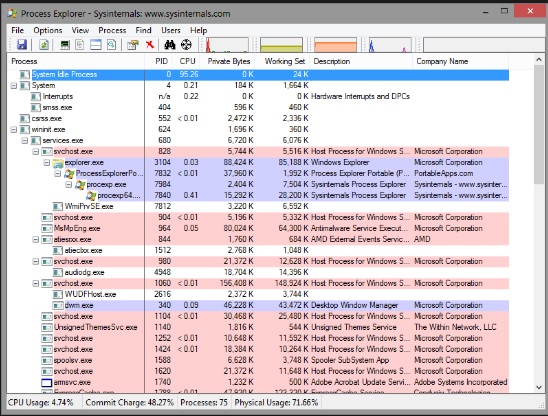
Malware Removal Process
In this chapter, we will understand how to go through the cleaning process of a computer, which has been infected by any type of malware. Let us follow the steps given below.
Step 1 − To begin with, we need to disconnect the computer from the network, which can be a cable connection or a wireless connection. This is done so that the hacking process loses connection with the hacker, so no further data can continue to leak.
Step 2 − Start the computer in Safe Mode, only the minimum required programs and services are loaded. If any malware is set to load automatically when Windows starts, entering in this mode may prevent it from doing so. This is important because it allows the files to be removed easier, since they are not actually running or active.
Starting a Computer in Safe Mode
Starting a computer in a safe mode can vary from Windows 7 to Windows 10. For the Windows 10 OS, the steps are as follows −
Step 1 − Press the Windows logo key + I on your keyboard to open Settings. If that does not work, select the Start button in the lower-left corner of your screen and then select Settings. Select Update & security → Recovery.
Step 2 − Under the Advanced startup section, select Restart now.
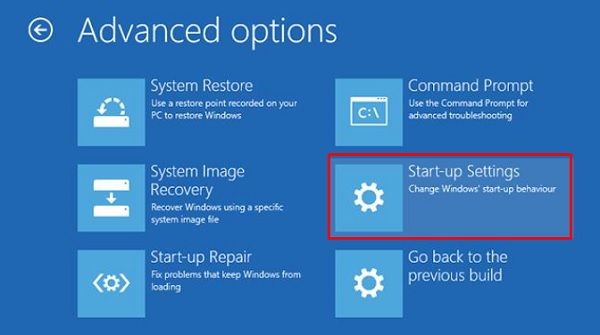
Step 3 − After your PC restarts to the Choose an option screen, select Troubleshoot → Advanced options → Startup Settings → Restart.
Step 4 − After your PC restarts, you will see a list of options. Select 4 or F4 to start your PC in the Safe Mode. If you need to use the Internet, select 5 or F5 for Safe Mode with Networking.
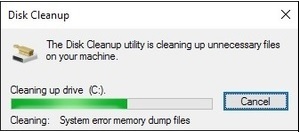
Delete Temporary files
Delete your temporary files. Doing this will speed up the virus scanning, free up disk space and even get rid of some malware. To use the Disk Cleanup Utility, included with Windows 10 just type Disk Cleanup in the search bar or after pressing the Start button and select the tool that appears – Disk Cleanup.
Stop the Malware Process that might be related to it
We will attempt to terminate all the associated malicious processes. To do this, we will use Rkill, which can be easily downloaded from the following link – www.bleepingcomputer.com/download/rkill/
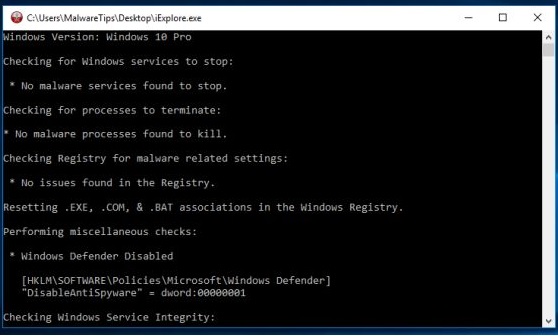
Download Malware Scanner and Start a Scan
If you already have an antivirus program active on your computer, you should use a different scanner for this malware check, since your current antivirus software may not have detected the malware. Most of the well-known antivirus software are given in the following screenshot.

Malware Removal - Protection
We should understand that viruses infect outside machines only with the assistance of a computer user, which can be like clicking a file that comes attached with an email from an unknown person, plugging a USB without scanning, opening unsafe URLs, etc. For such reasons, we as system administrators have to remove the administrator permissions of users in their computers.
Some of the most common don’ts for letting malware enter into a system are as follows −
- Do not open any email attachments coming from unknown people or even from known people that contain suspicious text.
- Do not accept any invitation from unknown people in social media.
- Do not open any URL sent by unknown people or known people that are in any weird form.
Some other important pointers for keeping your system updated are as follows −
- Keep updating the operating system at regular intervals.
- Install and update the antivirus software.
Any removable storage that is taken from third parties should be scanned with antivirus software that are updated. Also, keep in mind to check the following aspects as well.
- Check if your monitor is using a screen saver.
- Check if the computer firewall is on.
- Check if you are doing backups regularly.
- Check if there are shares that are not useful.
- Check if your account have full rights or restricted.
- Update other third party software.
Managing Malware Risks
Managing malware risks is mainly for those companies, who do not comply for single computer users. To manage the risk that comes from malwares, there some key factors that accept the technologies that are being used, there is a human factor too. Risk management has to do with the analysis that identifies malware risks and prioritizes them according to the impact that they can have on business processes.
To reduce malware risks in a midsize business environment, we should consider the following points −
- Common information system assets
- Common threats
- Vulnerabilities
- User education
- Balancing risk management and business needs
In the next chapter, we will learn some important malware removal tools.
Malware Removal - Tools
In the previous chapters, we have discussed what malwares are, how they function and how to clean them. However, in this chapter, we will see the other side of automated protection, which are classified as anti-malwares or antivirus. The usage of this piece of software is very important these days because as we saw in the earlier chapters, the number of malwares are increasing exponentially as a result, it is impossible to detect them.
Each anti-malwares producer have their own technologies and techniques on how to detect the malwares, but it is worth mentioning that the they are very fast to detect because they take updates almost every day with the new malware detections.
Some of the most globally renowned and effective anti-malware or antiviruses are mentioned below −
- McAfee Stinger
- HijackThis
- Malwarebytes
- Kaspersky Endpoint Security 10
- Panda Free Anti-virus
- Spybot Search & Destroy
- Ad-Aware Free Antivirus+
- AVG Antivirus 2016
- SUPERAntiSpyware
- Microsoft Security Essentials
-



Comments
Post a Comment